Performed by: Jeremy Rodriguez
This report documents the Security Risk Assessment of a data center facility owned by Regional Bank. This data center supports the Online Banking System used by Regional Bank. As such it is critical to day to day operations.
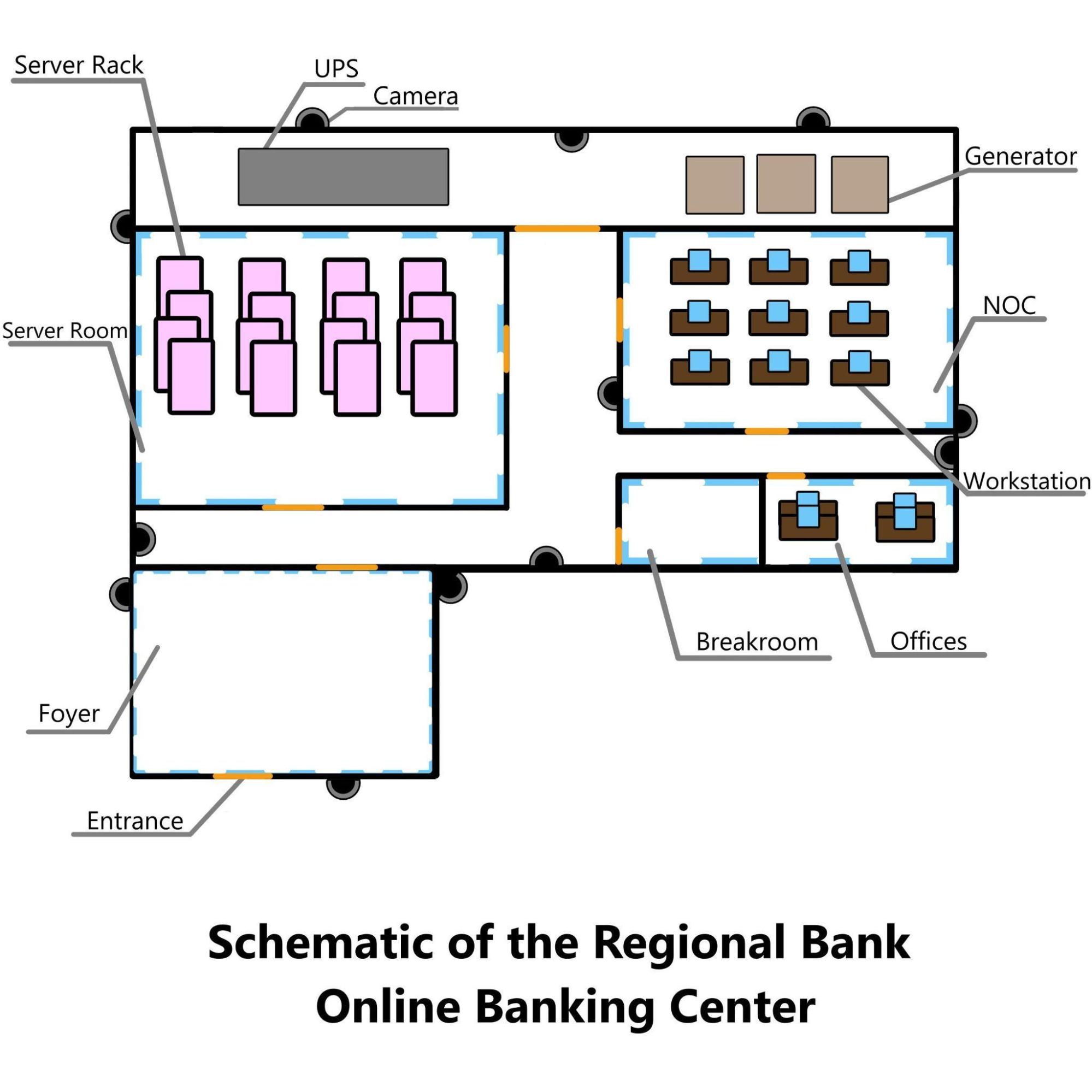
The data center facility being assessed in this report belongs to Regional Bank. Regional Bank’s organization is relatively new and consequently, relatively small. In order to provide a modern banking solution the organization has invested in a data center to support their Online Banking system. This new data center is relatively small and is briefly described here:.
Asset | Criticality | Vulnerability | CVE Site ID |
Servers | High | Azure Arc-Enabled Servers Escalation of Privilege Vulnerability | CVE-2023-38176 |
Generator | High | No access control methods | |
UPS | Medium | No access control methods | |
Workstations | Medium | make-ca is a utility and prior to version 1.10, make-ca misinterprets Mozilla certdata.txt and treats explicitly untrusted certificates like trusted ones | CVE-2022-21672 |
Cameras | Low | Vulnerable to both power and network outages |
2 ways to protect the physical assets.
2 ways to protect the cyber assets.
2 topics for an employee security training program for users with privileged access
The current security methods include security cameras, and pin pad locks on select doors. Unique passcodes are given to each employee who requires access. These cameras are consistently monitored by two security guards during operations. The NOC would also be aware if any device were to go down.
A generic physical security system is in place and the front entrance is locked overnight. An adjacent alarm is connected to the front door. All exterior windows are equipped with sensors that can detect if the glass is shattered.
A software Intrusion Detection System is in place running the default configurations.In addition a physical firewall device is placed between the inner network and ISP connection. The NOC is also always actively monitoring the network.
With the upgraded access control methods detection will be easier and faster. The security guard team will have more precise information on anomalies and can go in more prepared. The same goes for the NOC as the upgraded IDS will make the anomalies easier to find and respond to. During an event, upper management will be informed so that they can report the anomaly and secure further cybersecurity assistance if needed.
For a physical breach the response plan needs to involve law enforcement as soon as possible. Depending on the severity of the incident the security guards may be mobilized immediately or not at all. Upper management will also be informed so that information can be gathered for stakeholders and they can be briefed on the situation
For this type of breach the entirety of the NOC needs to be active in finding and responding to the breach. As soon as the breach is detected upper management needs to be notified so that more cybersecurity resources can be obtained if necessary. Upper management will also be informed so that information can be gathered for stakeholders and they can be briefed on the situation.
During the recovery phase the anomalous activity has been quarantined or dealt with. The next steps are intended to assure critical business functions remain accessible. Repudiation methods may be used to recover any lost data. Any physical assets that have been damaged are assessed and repaired/replaced depending upon severity. All bypassed security methods are also assessed for effectiveness and strengthened or repaired if necessary. HR and PR departments managing public relations are informed and/or mobilized to prepare public statements if necessary. Security policies are also investigated and adjusted to prevent a similar breach going forward.
The recovery plan for physical breaches needs to assess any bypassed access control methods for effectiveness. If they are found to be destroyed, or simply not effective enough, these methods should be upgraded or replaced.
Similar to physical recovery, access control methods need to be assessed. IDS systems need to be investigated including any firewall devices and the IDS software. Any faulty devices or software need to be investigated and/or reconfigured. Known vulnerabilities need to be addressed and if unknown need to be found. If data has been lost, backups need to be used to restore access to necessary resources immediately.
The overall security posture of the Regional Bank’s Online Banking Datacenter is mostly adequate but can be improved. Most importantly the policies in place address communication in a way that will make the recovery and response stages easier to achieve. The organization follows a security policy lifecycle for continuous improvement, and maintains the functionality of the Online Banking System. There is also a recovery and response plan in place in case of a disaster or breach.